Cracking Methodology:
- Extract hashes
- Format hashes
- Calculate the cracking time
- Prepare wordlist
- Attack the hash
Rule-based Attacks:
- ''.rule'-filer innehåller en särksild syntax som talar om för Hashcat hur den ska hantera dictionaries
\$<valfritt> = appendar valfritt
\^<valfritt> = prependar valfritt
c = stor första bokstav
- Reglerna läses från vänster till höger och tillbreds i den ordning de kommer
- Ny rad i regel-filen skapar en ny variation av ordet som också kommer testas
- Exempel på syntax:
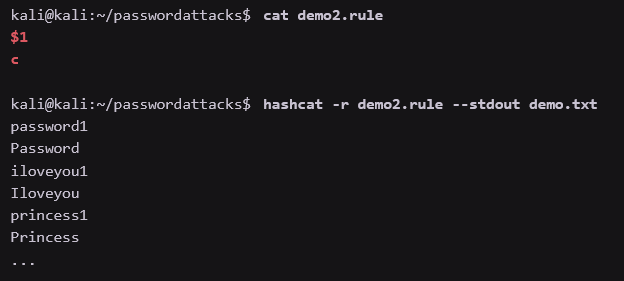
- Läs ut nya listan med hashcat så här:
hashcat -r regel.rule --stdout lista.txt
- Finns massor av bra regler under /usr/share/hashcat/rules/
Hashcat-crack commando:
hashcat -m 0 hash.txt /usr/share/wordlists/rockyou.txt -r regel.rule --force
- -m specificerar vilken hashtyp
- --force ignorerar felmeddelanden
Grep Hashcat Hash Type ID:
hashcat --help | grep -i "<sökning>"
Keyspace = Characters Possible x Password Length
Crack Time = Keyspace / Hash Rate
