6. Insecure System Components
SUID:
- To allow for users without permissions to access files such as /etc/shadow when changing their password effective UIDs are used.
- The real UID/GID is the one of the initiating script
- Inspect process using eUID:
ps u -C passwd
- Inspecting the UIDs:
grep Uid /proc/<PID>/status
- Find SUID binaries:
find / -perm -u=s -type f 2>/dev/null
- Instead of 'x' an 's' represents setuid for a specified file, such as:
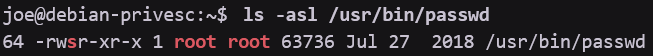
- If the SUID bit is set for execute that script or binary will always be executed as root
- Can be set with:
chmod u+s <filename>
Capabilities:
- More fine-grained privilege mechanism introduced in modern kernels
- Instead of giving an entire program elevated privileges, capabilities allow for only individual permissions instead of full root
- Searching for capabilities:
/usr/sbin/getcap -r / 2>/dev/null
- Search for the resulted capabilities in GTFOBins!
https://gtfobins.github.io/ - Exploit and win!
Sudo:
sudo -l
- Applications may be protected by AppArmor, check status with:
aa-status - Use GTFOBins!
Kernel:
- Enumerate the OS, kernel and architecture:
cat /etc/issue
uname -r
arch
- Craft a searchsploit query and find a good exploit:
searchsploit "linux kernel Ubuntu 16 Local Privilege Escalation" | grep "4." | grep -v " < 4.4.0" | grep -v "4.8"
- Compile the exploit to match the correct architecture and look out for compiling instructions. If possible wait to compile it on target machine itself.
- Transfer the binary to the target machine using SCP:
scp cve-2017-16995.c joe@192.168.123.216:
- Inspect the file to see if everything is correct before running, especially the architecture:
file cve-2017-16995
- Exploit and win!
Try PwnKit!