1. Offsec Recommendations
1. Executive summary
- Big picture
- Scope of engagement
- What was tested?
- Anything dropped from scope?
- Timing issues, eg. insufficient testing time
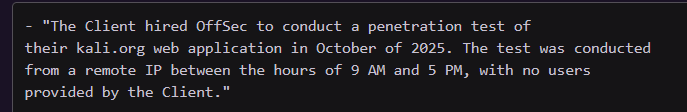
- Refer back to scope
- Time frame of test
- Time spent testing
- Dates
- (Testing hours)
- Rules of Engagement (ROE)
- Refer to referee on the team if any
- State the chosen ROE
- Supporting infrastructure and accoutns
- User accounts given
- IP addresses used to attack
- Note created accounts
Example:

2. Testing summary
- High level overview of each step of engagement
- Includes:
- Severity
- Context
- Worst-case scenario
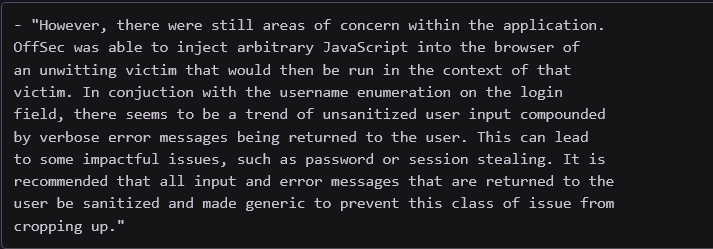
- Note any trends observed to provide strategic advice
- Mention things done well
- No absolute claims, eg. don't use "impossible"
- Ending with engagement wrap-up
Example:


3. Technical Summary
Structure:
- User and Privilege Management
- Architecture
- Authorization
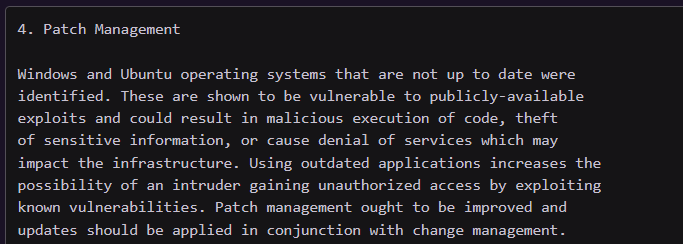
- Patch Management
- Integrity and Signatures
- Authentication
- Access Control
- Audit, Log Management and Monitoring
- Traffic and Data Encryption
- Security Misconfigurations
Example:
Finish with risk heat map based on vulnerability severity adjusted to clients context. Consulate with risk management if possible.
4. Technical Findings and Remediation/Recommendation
- Often presented in a table
- Describe vulnerability.
- Why is it dangerous?
- What can be accomplished using it?
- Technical details about vulnerability.
- Basic explanation of vulnerability and how to exploit it
- Proof of exploit, eg. appendix with notes and images
- Remediation
- Practical suggestions
- Detailed enough for system and application admins
- Clear, concise, thorough
Example:

5. Appendices
- List of compromised users
- Affected areas
- Proof-of-concept code blocks
- Technical write-ups
- Further Information
- Articles that describe vulnerabilities in-depth
- Remediation standards